Improve the Security of your Software Development Process, designed for Small and Medium Businesses

Improve the Security of your Software Development Process, designed for Small and Medium Businesses

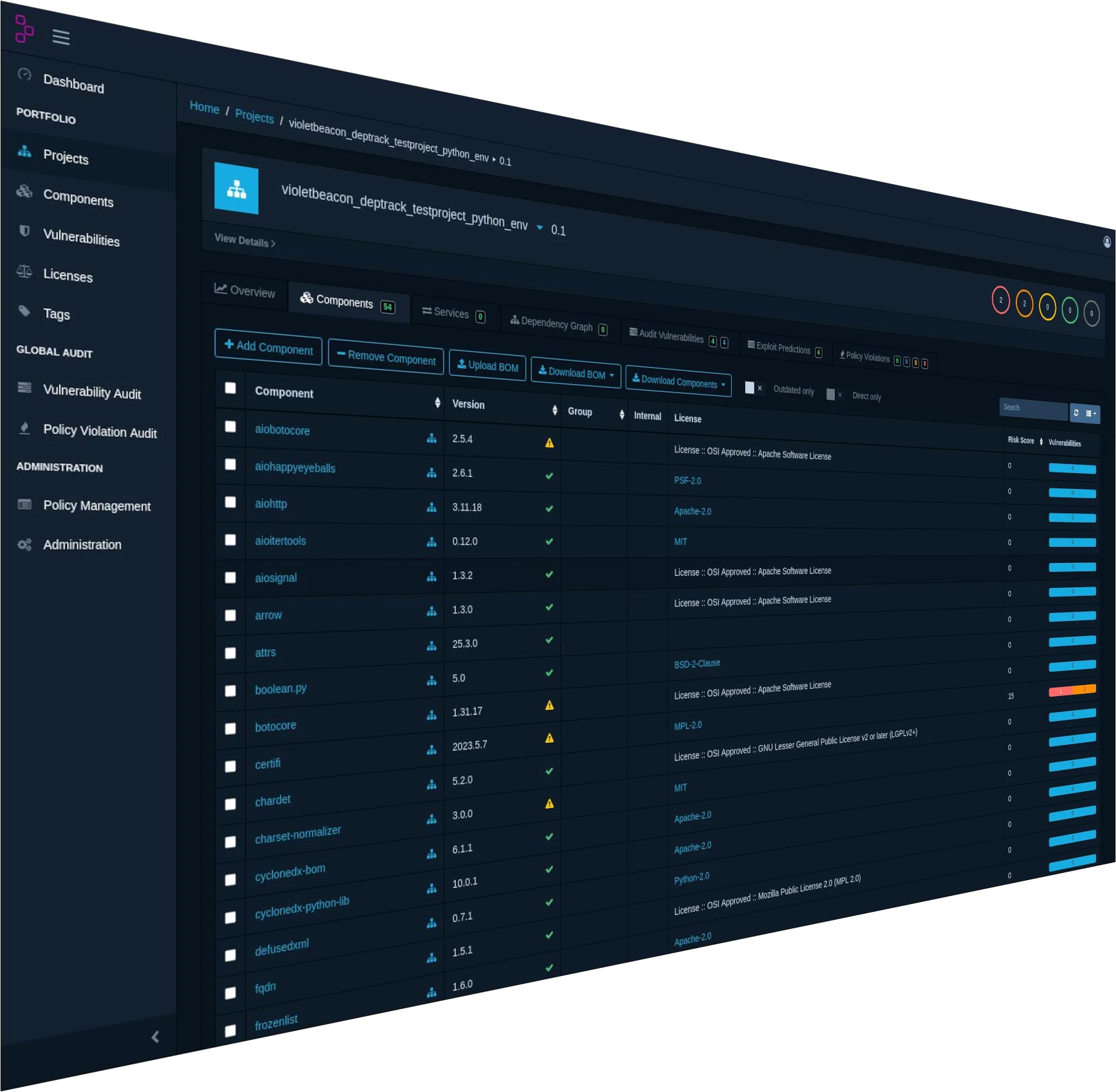
An SBOM is a comprehensive inventory that lists all the software components, libraries, and dependencies used in an application or system. It includes details like component names, versions, suppliers, licensing information, and relationships between components. Think of it as an "ingredient list" for software that provides complete transparency into what's actually running in your applications.
Regulatory Compliance: Government mandates like the US Executive Order on Cybersecurity now require SBOMs for federal software procurement. Many industries are moving toward similar requirements, making SBOMs essential for maintaining business relationships and avoiding regulatory penalties.
Rapid Vulnerability Response: When a new security vulnerability is discovered, SBOMs allow you to instantly identify which applications and systems are affected. This dramatically reduces the time from vulnerability disclosure to remediation, minimizing your exposure window.
Supply Chain Risk Management: SBOMs help you understand exactly what third-party code you're depending on, enabling better vendor risk assessments and helping you avoid components from untrusted or compromised sources.
License Compliance and Legal Protection: Track all open-source licenses across your software portfolio to avoid costly legal disputes, ensure you're meeting license obligations, and make informed decisions about component usage based on license compatibility.
Customer Trust and Transparency: Many enterprise customers now require SBOMs as part of their vendor security assessments. Providing accurate SBOMs demonstrates security maturity and can be a competitive advantage in sales processes.
Incident Response and Forensics: During security incidents, SBOMs provide crucial information for understanding attack vectors, assessing damage scope, and implementing containment measures quickly and effectively.















VioletBeacon and Dependency-Track can help your organization meet the following information security standards (as applicable to your adopted standards, policies and procedures):